A THREE STEP SECURITY EVALUATION PROGRAM TO ENSURE HIPAA COMPLIANCE AND BEYOND
UNDERSTANDING THE HIPAA SECURITY EVALUATION STANDARD
Covered entities that must comply with the Health Insurance Portability and Accountability Act (HIPAA) Security Standards are required to have completed implementation of the necessary safeguards by April 20, 2005. These technical and non- technical safeguards are intended to secure the access and transmission of electronic protected health information (e-PHI). The purpose of the Evaluation Standard in the HIPAA Security Regulation is to ensure that the covered entity appropriately maintains its security policies, procedures and technical safeguards.
Without a comprehensive Evaluation Program, a covered entity will not only risk non-compliance with this standard but could also fall out of compliance with other standards in the Regulation.
The HIPAA Security Evaluation Standard requires each covered entity to evaluate future changes in operations and the environment so that security of electronic protected health information is not compromised. Evaluations must be performed periodically and in response to environmental changes, operational changes, or an event that requires a change in its policies or procedures that affect e-PHI. The regulation does not address who should perform these Evaluations.
The program can be run by either internal staff or external consultants or a combination, but a comprehensive Evaluation program must be established.
Changes in the environment and operations can be defined as:
- Technical Environment (Hardware, Software and Media)
- Non Technical Environment (Physical location and Facilities)
- Operations (People and Process)
Using the above as working definitions, it is easier to understand where an organization needs to concentrate its efforts. It also clarifies the direction of the regulators toward policy and procedure. If an organization reviews policy and procedures as defined above, any technical changes will also be identified in the review process.
A comprehensive program should begin with an Initial Evaluation that will establish a compliance baseline to be used for measurement in future evaluations. The Initial Evaluation will be followed by the development of a Continuing Evaluation process.
The Continuing Evaluation component would review planned changes in the environment for any affect on data security. The last required element of the program is to conduct a Periodic Evaluation of policy and procedures for needed updates in order to maintain compliance. This three-step approach ensures that any new technology or operations the organization adopts will take into account the potential impact on security of e-PHI.
SECURITY EVALUATION THREE-STEP APPROACH
The recommended Security Evaluation program consists of three components: 1) Initial Evaluation post implementation, 2) Continuing Evaluation, and 3) Periodic Evaluation.
Each of these components is designed to validate that current operations are conducted in a compliant environment. There are several advantages to this three-step approach:
- Ensuring a continuum of compliance (better data security)
- Reduced probability of remediation (lower cost)
- Less complex Evaluations (incremental and manageable)
- Less time commitment for staff (lower cost)
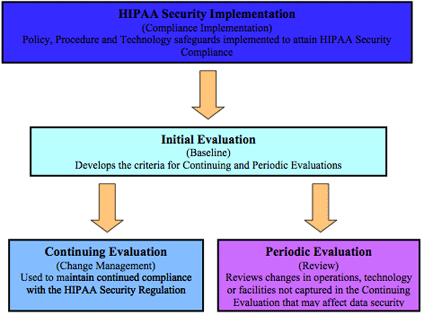
The Initial Evaluation is a review of policy, procedure and technological safeguards the organization has implemented to satisfy the HIPAA Security Rule requirements. The Evaluation is done to provide a comprehensive compliance baseline to validate compliance and to develop a baseline standard against which future change can be measured. The areas on which the Initial Evaluation should focus are technology, operations, policies and procedures pertaining to electronic protected health information. A baseline is established when the organization is satisfied that its operations are meeting the HIPAA Security Standards requirements. Any future evaluations will be measured against this baseline and reviewed only for changes affecting activities associated with complying with the standards.
Once the organization is confident that it is operating in a state of compliance, it is important to begin a Continuing Evaluation program to maintain compliance. The HIPAA Security Rule requires the covered entity to evaluate its compliance in light of any changes in the environment. An organization that seeks to maintain compliance and wants to control cost and risk will need to integrate Security Evaluation into its environmental change management and demand management processes. This should include environmental changes concerning regulations, technology, operations and facilities.
In addition to the Initial and Continuing Evaluations, the HIPAA security rule requires each organization to complete a Periodic Evaluation to ensure that changes in the environment did not compromise its compliance. These are technical and non-technical changes as they relate to regulation, technology, operations and the physical environment. As was discussed earlier, the Periodic Evaluation will utilize the baseline information and evaluate changes in the environment that may affect the organization's security.
INITIAL EVALUATION OR BASELINE
The covered entity has likely gone through months, if not years, of preparation for HIPAA Security compliance. It is important to validate that the effort was successful and to develop a baseline against which future Evaluations may be measured. A complete review of current operations as they relate to the use and security of electronic protected health information is an important step in accomplishing this goal. In larger organizations it is difficult to review activities at the same time that you are developing the safeguards necessary to meet compliance standards. This component will require the greatest effort to complete, but is critical to the success of the program.
A department-by-department review of operations that access and transmit e-PHI, as well as those areas responsible for maintenance of the technical safeguards will accomplish this requirement. Technical environment changes, such as an increase in the number of unauthorized attempts at system access, should also be scrutinized. Unlike the risk analysis required by section 164.306(a)(1)(ii)(A), the Initial Evaluation looks at what the organization implemented for compliance measured against the regulation's standards. This includes the review of policy, procedure and technical safeguards as they are deployed in the entity's operational environment. When completed, the Initial Evaluation will produce the solid baseline necessary for the organization to measure change. The key to the success of this component is a clear understanding of the organization's operational activities and which activities are affected by the HIPAA Security Standards. This understanding is necessary to allow the organization to appropriately determine if the implemented safeguards are adequate to ensure organizational compliance.
CONTINUING EVALUATION
Once the baseline is established, the Continuing Evaluation process should be developed and implemented to maintain sustainability of HIPAA Security compliance. Systematic and controlled reviews of changes that affect data security are necessary for a comprehensive Evaluation Program. Each organization must identify, train and assign individuals to key processes associated with technology and operations change. These individuals would be involved in the initial phases of project development to review proposed projects for HIPAA Security concerns and assist in the development of alternatives where appropriate. The parties accountable for this activity should be key players in the change and demand management processes of the organization. If these processes do not currently exist, this is a good time to develop, formalize and document them for future change and demand management.
After a project has completed the environmental change and demand management processes and is approved for development, security subject matter experts will conduct a final review of the project prior to its implementation. In this final review they will look for any modifications to the project that might affect HIPAA Security compliance. Questions to determine impact will be asked by the evaluators and answered by the project champion.
The first question that needs to be answered is "Will the project/process use, view or transmit e-PHI in any way?" This is important because the answer to this question will determine the need for gathering additional information. A "yes" answer will lead to questions about specific regulatory requirements pertaining to access controls, data transmission security, reporting on system activity, and policy modification. At a high level, additional questions will be:
- Is access to data containing e-PHI affected?
- Is access to facilities or equipment containing e-PHI affected?
- Is transmission of e-PHI affected?
- Is system activity review concerning e-PHI affected?
- Are modifications to existing or new policies and procedures required to sustain HIPAA Security Compliance?
As these questions are answered in the affirmative they too will require an additional layer of detailed information to ensure that compliance is not negatively impacted. Subject matter experts (SME) for technology and regulatory compliance should be included in this process whenever the answer to any of these additional questions is "yes." These SMEs will be able to determine the detailed information requirements necessary to address potential HIPAA Security concerns.
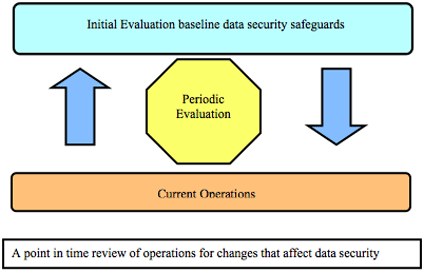
PERIODIC EVALUATION
Formal Periodic Evaluation is a required standard of the HIPAA Security Regulation. If the organization has completed the Initial Evaluation and initiated the Continuing Evaluation process, this portion of the Evaluation process should be quite painless. A covered entity is required to perform technical and non-technical evaluations in response to environmental or operational changes affecting the security of e-PHI that establishes the extent to which an entity's security policy and procedures continue to meet the requirement. Simply stated, the entity must evaluate changes in the environment both technical and non-technical (operational) in nature to see if the policies and procedures initially implemented to meet the regulatory requirements are still adequate.
Since the Continuing Evaluation process should capture all planned changes throughout the organization, it will be necessary for this component to identify those changes not captured by the organization's planning process. Again, it is critical to the success of the Periodic Evaluation that a clear understanding of the operational activities resides with the evaluators. The ability to determine activities that have been missed but may have an adverse effect on HIPAA Security requirements is essential for the success of this particular component. Included in environmental changes should be any remediation projects that were identified in any previous Evaluation processes. These remediation projects should be a part of the next scheduled Periodic Evaluation process after their implementation to ensure the vulnerability was successfully resolved.
The key concern in this section centers on the policies and procedures. When a gap is discovered, the activity or the policies and procedures affected by the change must be modified. The questions that are used to evaluate changes that were not identified by the Continuing Evaluation process are essentially the same.
NEXT STEPS
Once a potential vulnerability has been identified in any of the Evaluation processes, the results are presented to the entity's Chief Information Security Officer (CISO). The CISO should determine responsibility for the development of a specific remediation plan. This will ensure a coordinated effort and prevent the development of conflicting or redundant solutions. The party responsible for each specific remediation plan will need to document the following:
- Evaluation results
- Who is responsible for developing the solution
- Description of the proposed solution
- Dates of key milestones for the remediation project
- Expected results
The next Periodic Evaluation that is performed after successful implementation of any remediation projects will review these projects for compliance and completeness. If a project is scaled such that it will not be completed prior to the next review, the reason should be documented in its project plan. The inclusion of completed remediation projects ensures that identified needs are correctly addressed for the continuance of HIPAA Security compliance
FINAL THOUGHTS
It is important for the organization not to lose sight of the importance of how e-PHI is used by the organization's operations. This is just as critical to the security of the data as the technological safeguards protecting it. State-of-the-art data security only works if the people using the data follow the procedures related to its use.
In conclusion, constant vigilance to review the impact of change is the key to success of any regulatory compliance effort. When regulatory compliance is coupled with the world of technology, where change is constant, diligent monitoring of process change is essential. The three-step Evaluation process recommended here will allow an organization to position itself to maintain security and compliance in a dynamic and challenging environment.
Print or Download
Download this document in PDF format to print or read off-line.